De nombreux professionnels aimeraient utiliser le protocole Remote Desktop Protocol (RDP) comme pierre angulaire de leur environnement industriel, afin de permettre la surveillance, la configuration et le dépannage à distance de systèmes critiques tels que les automates programmables, les IHM et les serveurs SCADA.
RDP est un protocole de communication réseau appartenant à Microsoft qui permet aux utilisateurs de se connecter à distance à un autre ordinateur. Il s'agit d'un protocole accessible et standard, mais sa commodité s'accompagne d'une lourde responsabilité en matière de sécurité.
Dans le paysage actuel de la cybersécurité, laisser RDP non sécurisé revient à donner les clés de sa maison à des inconnus. Une connexion RDP compromise peut paralyser les opérations, perturber les chaînes de production et même compromettre les protocoles de sécurité.
Les risques de sécurité de RDP se cachent dans l'ombre
Le protocole RDP présente un large éventail de risques pour la sécurité :
- Surfaces d'attaque du réseau : Pour que le protocole RDP fonctionne, vous devez laisser les ports de votre appareil ouverts sur le réseau. Malheureusement, RDP est souvent fourni avec des paramètres par défaut faibles, tels que l'authentification de niveau réseau (NLA) désactivée et des mots de passe faciles à deviner, ce qui le rend vulnérable aux attaques par force brute.
- Accès illimité : Par défaut, RDP autorise l'accès à partir de n'importe quelle adresse IP externe, ce qui augmente la surface d'attaque et votre potentiel d'attaque.
- Mouvement latéral : À partir de votre système compromis, ils peuvent pivoter pour accéder à d'autres actifs précieux au sein de votre réseau.

Les processus traditionnels de sécurité RDP ne suffisent pas
Traditionnellement, les experts en sécurité recommandent de prendre les mesures suivantes pour renforcer votre accès RDP :
- Activer l'authentification au niveau du réseau (NLA): Cette option ajoute une couche de sécurité supplémentaire en exigeant l'authentification de l'utilisateur avant l'établissement d'une connexion.
- Restreindre l'accès et les ports: Limitez l'accès RDP à des adresses IP et à des ports spécifiques afin d'éviter que des tentatives aléatoires n'atteignent votre système.
- Utilisez des mots de passe forts et l'authentification multifactorielle (MFA): Les mots de passe complexes et l'authentification multifactorielle constituent un obstacle de taille pour les attaquants, qui ont ainsi beaucoup plus de mal à percer vos défenses.
- Maintenez-le à jour: Il est essentiel de corriger rapidement les vulnérabilités, car les logiciels obsolètes constituent un point d'entrée facile pour les exploits.
- Envisager des alternatives: Envisagez des alternatives sécurisées telles que les VPN ou les solutions d'accès à distance dédiées, en particulier pour les scénarios à haut risque. Dans la pratique, très peu d'organisations autorisent le RDP sans passer par un VPN. Mais le coût/complexité du VPN apporte ses propres problèmes, et les VPN ont récemment connu des problèmes qui ont rendu leur protection inutile. C'est particulièrement mauvais si la configuration RDP est lâche/ouverte parce qu'elle est protégée par le VPN.
Malheureusement, aucune de ces mesures n'est infaillible. Les surfaces d'attaque du réseau restent ouvertes et les attaquants peuvent passer d'un système à l'autre. Et bien que les VPN chiffrent vos données, ils peuvent être lents, peu fiables et poser des problèmes de confidentialité en fonction du fournisseur et des pratiques de l'utilisateur.
La solution idéale pour renforcer vos systèmes distants consiste à résoudre tous les problèmes de sécurité tout en autorisant un accès RDP complet. Il n'y aurait aucune surface d'attaque (aucun port exposé), toutes les données seraient cryptées, l'accès ne serait accordé qu'aux personnes authentifiées par cryptographie et les mouvements latéraux ne seraient pas autorisés (à moins qu'ils ne le soient).
Cela vous semble impossible ? Ce n'est pas le cas avec SSH No Ports.
Renforcez votre sécurité RDP avec SSH No Ports
La solution SSH No Ports d'Atsign élimine ce risque en créant un tunnel sécurisé qui est instancié à l'aide d'un plan de contrôle crypté. Imaginez cela comme un couloir privé pour vos données, protégé par des clés uniques stockées en toute sécurité sur vos appareils.
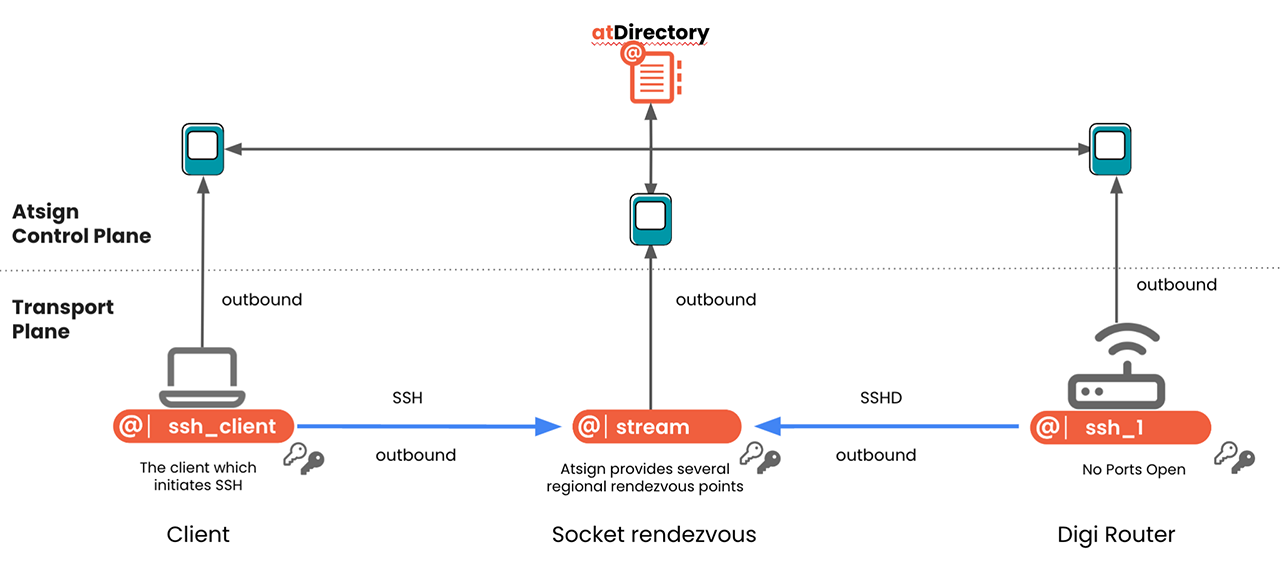
Sécurité RDP renforcée avec SSH No Ports :
- Plus de ports exposés : SSH No Ports supprime le besoin de ports réseau exposés, une cible courante pour les attaquants. L'élimination de cette vulnérabilité renforce considérablement votre position de sécurité RDP.
- Cryptage de bout en bout : Toutes les données transmises par le tunnel sont cryptées à l'aide de clés coupées à la périphérie. Cela garantit la confidentialité, même en cas d'interception par des acteurs malveillants.
- Authentification cryptographique : Chaque tentative d'accès est vérifiée à l'aide de méthodes cryptographiques robustes, ce qui permet de bloquer les utilisateurs non autorisés et de sécuriser davantage votre système.
- Réduction des mouvements latéraux : Lorsqu'ils sont mis en œuvre sur tous les appareils du réseau, les mouvements latéraux sont pratiquement éliminés.
Contrairement aux méthodes traditionnelles, SSH No Ports élimine la nécessité d'une configuration complexe du pare-feu ou de la gestion de nombreux mots de passe. Cela simplifie la gestion de la sécurité et rationalise le contrôle d'accès.
Utilisation de RDP avec SSH No Ports
Avec SSH No Ports, l'accès RDP transparent est facile :
- Créer le tunnel sécurisé: Le client SSH No Ports crée un tunnel crypté vers le serveur RDP distant, établissant ainsi une connexion sécurisée.
- Tirez parti de votre RDP habituel: Votre client RDP existant se connecte en toute sécurité via ce tunnel crypté, vous offrant ainsi l'expérience RDP à laquelle vous êtes habitué.
Au-delà de RDP : Une solution polyvalente
Les avantages de SSH No Ports ne se limitent pas à RDP. Il peut établir des connexions sécurisées pour n'importe quel protocole TCP, tel que VNC, HTTPS, ICA, etc.
Déploiement simplifié avec les routeurs Digi
Le déploiement de SSH No Ports comprend deux éléments clés :
- SSH No Ports Daemon : Il fonctionne sur votre routeur Digi IX40 ou Digi EX50 dans un conteneur Digi sécurisé pour une protection accrue.
- SSH No Ports Client : Ce client facile à installer est disponible pour diverses plates-formes, notamment Linux, MacOS et Windows.
Avec SSH No Ports, vous pouvez atteindre un nouveau niveau de sécurité et de facilité d'utilisation pour l'accès à distance. Éliminez les ports exposés, tirez parti d'un cryptage robuste, bénéficiez d'une prise en charge polyvalente des protocoles et d'un déploiement simplifié, le tout dans une solution complète.
Pour plus d'informations et une version d'essai gratuite de 2 semaines de SSH No Ports, visitez www.Noports.com dès aujourd'hui .
Prochaines étapes
A propos de l'auteur
 Colin Constable est cofondateur et directeur technique d'Atsign, une entreprise pionnière en matière de solutions d'accès à distance sécurisé telles que NoPorts. Cette technologie innovante permet d'établir des connexions sécurisées avec des appareils sans ports exposés, ce qui réduit considérablement la surface d'attaque des pirates. Avec plus de 40 ans d'expérience dans le domaine de la technologie, Colin dirige Atsign dans la construction d'un Internet plus sûr et plus privé.
Colin Constable est cofondateur et directeur technique d'Atsign, une entreprise pionnière en matière de solutions d'accès à distance sécurisé telles que NoPorts. Cette technologie innovante permet d'établir des connexions sécurisées avec des appareils sans ports exposés, ce qui réduit considérablement la surface d'attaque des pirates. Avec plus de 40 ans d'expérience dans le domaine de la technologie, Colin dirige Atsign dans la construction d'un Internet plus sûr et plus privé.